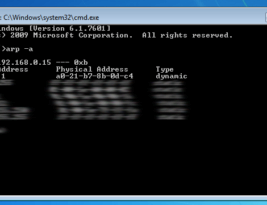
Quite a few netgear devices come with a hidden page that you can browse to, this will then enable Telnet access on the device. However …
Category: Networking
I have already done a post about getting telnet access on to your DGND3700 netgear router, however you can also play around with some settings …
Traditionally Cisco based NAT on routers and firewalls was done in a fairly singular direction by defining two interfaces one as “inside” and the other …
Asterisk and FreePBX is an Open Source PBX which can be installed on Linux, and is commonly used to provide PBX services via VoIP (Voice …
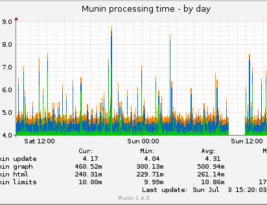
Munin is a great open source tool for graphing performance metrics (amongst other things) of your linux hardware. It’s not the most intuitive of tools to use …