Scan your webserver with Nikto
 Targeted hacking attacks are almost impossible to stop as the likes of Sony found out recently, however you can certainly try protect yourself against the 'script kiddies' that are just attacking web servers using public exploits.However you need some way of checking your web server against this known list of exploits, as you can imagine this list is quite big that's why we use Nikto.
Targeted hacking attacks are almost impossible to stop as the likes of Sony found out recently, however you can certainly try protect yourself against the 'script kiddies' that are just attacking web servers using public exploits.However you need some way of checking your web server against this known list of exploits, as you can imagine this list is quite big that's why we use Nikto.
First you need to install the software:
apt-get install nikto
Next you just need to start the scan going against your web server.
nikto -h http://localhost
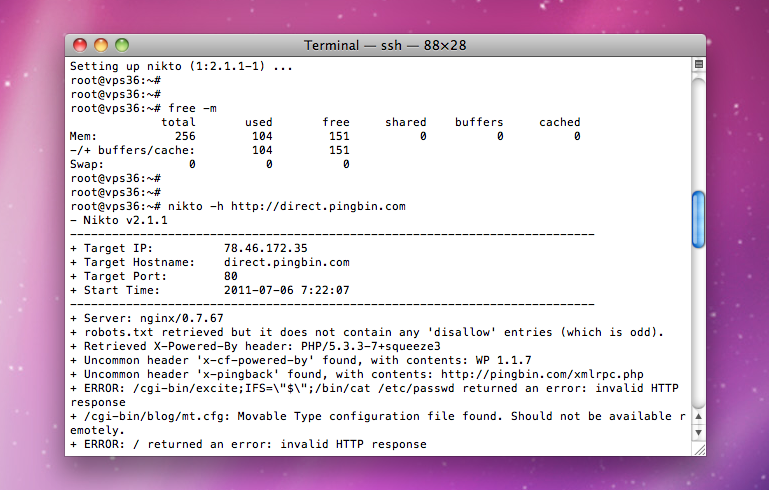
After a few minuets you should get a report like the following:
- Nikto v2.1.1
---------------------------------------------------------------------------
+ Target IP: 78.46.172.35
+ Target Hostname: direct.pingbin.com
+ Target Port: 80
+ Start Time: 2011-07-06 7:22:07
---------------------------------------------------------------------------
+ Server: nginx/0.7.67
+ robots.txt retrieved but it does not contain any 'disallow' entries (which is odd).
+ Retrieved X-Powered-By header: PHP/5.3.3-7+squeeze3
+ Uncommon header 'x-cf-powered-by' found, with contents: WP 1.1.7
+ Uncommon header 'x-pingback' found, with contents: http://pingbin.com/xmlrpc.php
+ ERROR: /cgi-bin/excite;IFS=\"$\";/bin/cat /etc/passwd returned an error: invalid HTTP response
+ /cgi-bin/blog/mt.cfg: Movable Type configuration file found. Should not be available remotely.
+ ERROR: / returned an error: invalid HTTP response
+ 3818 items checked: 19 item(s) reported on remote host
+ End Time: 2011-07-06 7:31:07 (527 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Have a read through it, if you find anything that looks dodgy just put it in google and there are normally always some suggestions on how to fix it, or leave me a comment here :)
NOTE: ONLY do this against a web server that you own and do it via localhost, doing this against other peoples servers could be considered hacking, and could be illegal in your area!